Sentinel ARC integration
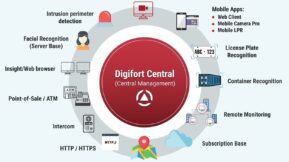
The Digifort open platform VMS is integrated with Sentinel, the most popular Alarm Receiving Centre (ARC) and remote monitoring station software platform, in the UK.

Sentinel is designed to give operators a consistent, alarm handling ‘dashboard’ interface, irrespective of the CCTV, intruder, environmental and lone worker systems being used.
On receipt of alarms and events from the Digifort system, Sentinel can be configured to respond in different ways. The following are some examples:
- Highlight the alarm, so that an operator can make an immediate response, including stacking and prioritizing alarms.
- Connect to the site for alarm verification.
- Enable on site PTZ control, whilst in the alarm state.
- Enable audio announcements, which can correlate with an individual camera or zone on site (zoned audio).
- Listen for noises on site, using a microphone, which can be on a per camera basis.
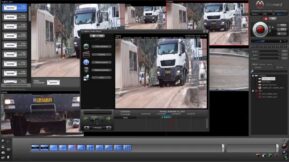
The advantage of Digifort operating alongside the Sentinel ARC software, is that many additional video management, analytics and reporting features can be enabled, significantly enhancing system functionality. For instance, where a Sentinel operator at the ARC might be alerted to an alarm for a real-time response, Digifort can concurrently send real time video alerts to an extensive hierarchy of designated keyholders, users and operators.
Digifort also includes a “Global Event” feature to enable a different set of responses to alarms, if the system has already been triggered from elsewhere and is already in an alarm state. This might be from integrated video analytics, PIRs, access control and motion detection systems, but can also include wider network management functions like failover status and network connection status.
Global Events can be triggered in many ways, including from:
- Digifort video analytics alarms.
- Intrusion detection alarms from third-party PIRs, access control and sensor systems.
- Motion detection alarms from cameras or from the server-based, Digifort system.
- When the Digifort system goes into failover and failback mode.
- When the connection to a camera, I/O module, or other monitored device is lost and / or re-instated.